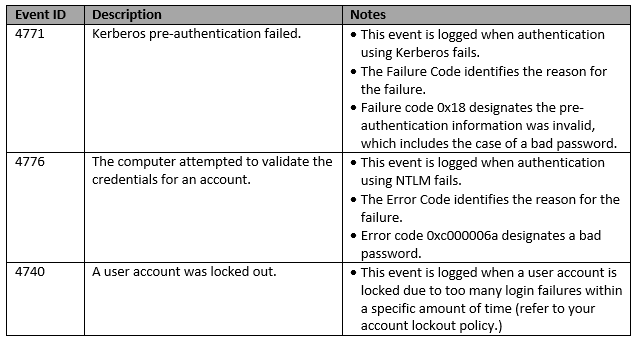
Working as both an AD Domain Admin and Splunk Admin, I am working on an Active Directory app for Splunk to present useful statistics as well as provide search forms and reports to be used by AD and Help Desk support staff.
This is the first in a series of blog posts I will make on the development of this app.
Step 1: Identify which Event IDs are related to logon failures and lockouts.
Step 2: Contruct the search strings that will be used to perform relevant searches
- index=“ad” source=”WinEventLog:Security” Account_Name=<accountname> EventCode=4771 Failure_Code=”0x18″ earliest=<-4h> | table _time Client_Address Account_Name EventCode Failure_Code
- index=“ad” source=”WinEventLog:Security” Logon_Account=<accountname> EventCode=4776 Error_Code=”0xc000006a” earliest=<-4h> | table _time Source_Network_Address Logon_Account EventCode Error_Code Logon_Type
- index=“ad” source=”WinEventLog:Security” Account_Name=<accountname> EventCode=4740 earliest=<-4h> | table _time Caller_Computer_Name Account_Name EventCode
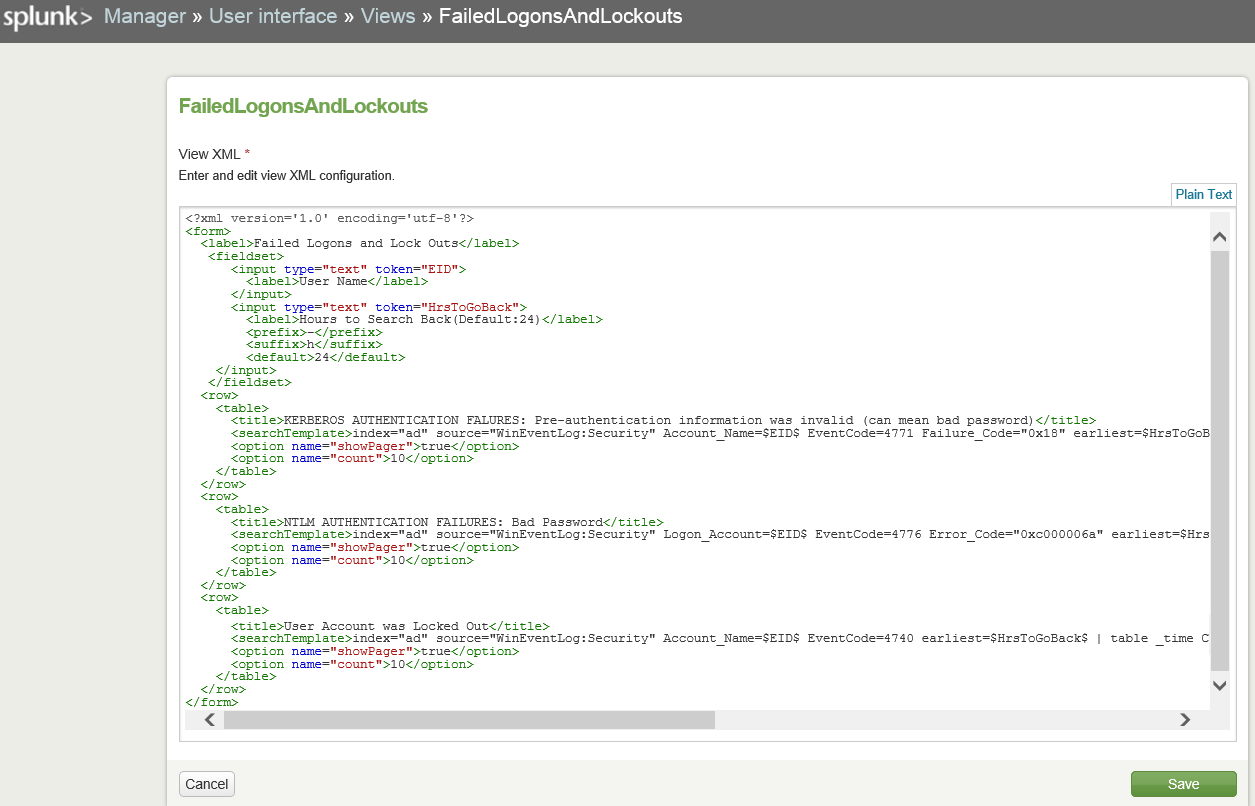
Step 3: Create a search form in Splunk
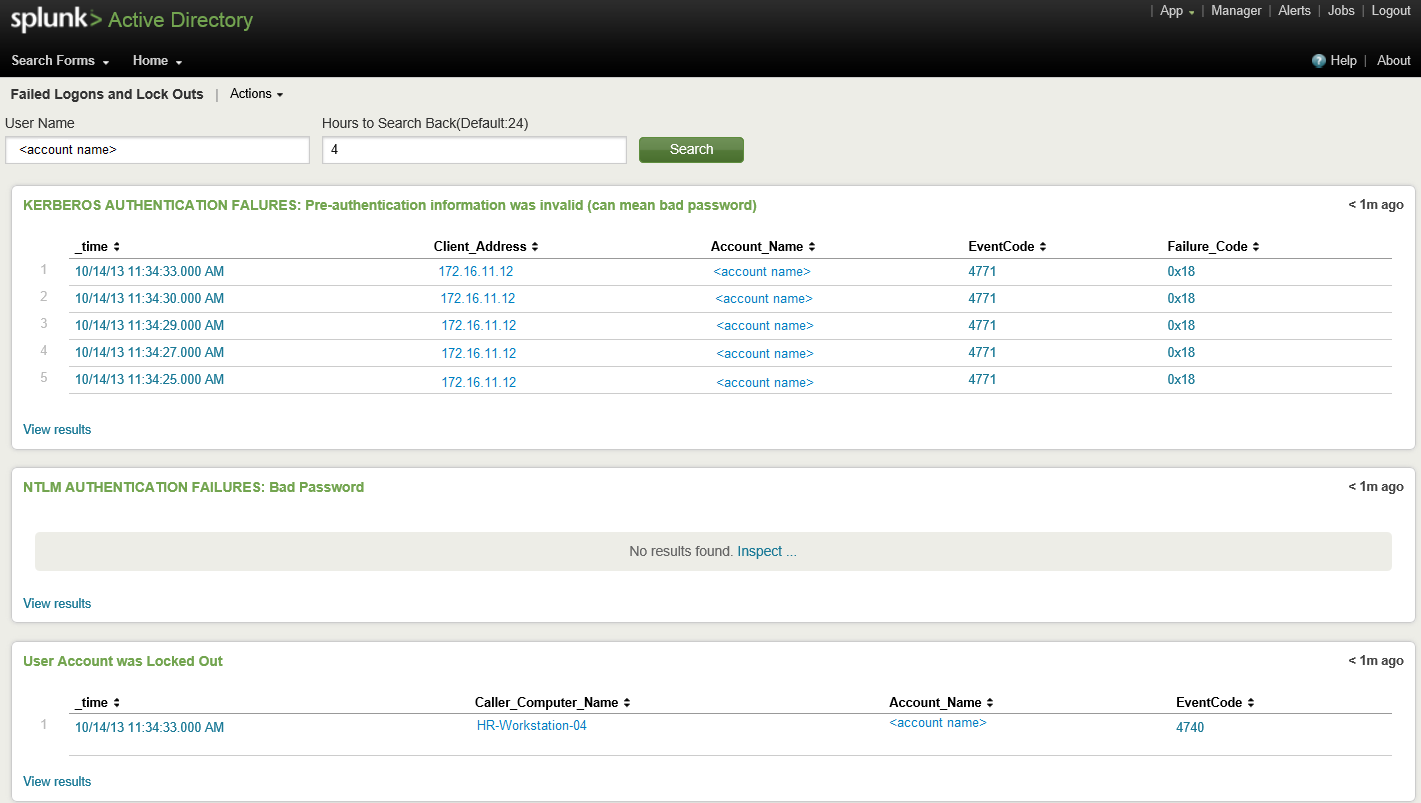
The search form that I created includes two input fields: account name and how many hours to search back. The input tokens are plugged into the search strings to customise the search.
Search Form:
Would be nice if you can share the code.